Structured Query Language (SQL) is a programming language used to organize the databases and execute different mathematical operations on the data collected. It was created in the 1970s and is is widely used by administrators and developers, who have to create scripts and perform data analysis using this language. To run queries, designers can also use this.
What are SQL Injection Tools?
Structured Query Language Injection, also known as SQLI, is a mutual bout course that uses spiteful SQL code for back-end database handling to approach the critical information, not be exposed otherwise. This information may comprise any number of objects having complex company data, worker lists, or private client particulars.

The inspirational SQLI can be can be important for tech-persons but out of the reach for other persons. If attacked by a hacker, your user list can be shown to hackers without authorization. And in some situations, they may remove your entry table record. Also, they may take the admin control of your data-bank, that might affect your business. While considering the cost of SQLI, the main cost is incurred on loss of a customer’s trust, their credentials like mobile numbers, credit details, addresses, etc.
Types of SQL Injections
SQL injections traditionally drop under three types. You can categorize SQL injection sorts based on how they approach back-end data and their expected harms. These three types are:
- In-band SQLI
- Inferential (Blind) SQLI
- Out-of-band SQLI
List of SQL Injection Tools
There are a few free-to-use SQL injection tools that you can use. These tools are robust and can execute automated SQL injection operations against special applications. You can also download these SQLI from their official pages. The list of best and very famous SQL injection tools are:
1. Havij
Havij is considered the best automatic SQLI tool that assists penetration testers in searching and using SQLI compulsion on a web page. This tool is completely automated and created by ITSecTeam, an Irani company. The name of this tool highlights Carrot that is the symbol tool. The GUI of this tool is easy to use and comprehend. Due to this, it is helpful for the admin to retrieve the related information. The purpose of this tool is to protect from threats by the coders, hackers, and non-tech users.

Highlights
- In the commercial version, you get the Blind MSAccess.
- It also provides the PostgreSQL.
- Easy to get a user guide, and users can eliminate the record.
- Supplementary removal of data file function.
- XML layout with the tool for data storage.
- The settings can be modified at any time.
- Re-pairings are available to shield the weaknesses of the site.
2. BBQSQL
BBQSQL is a SQL tool to assist Web Safety experts in discovering Time-based Blind SQL Injection on HTTP Slogans and the misuse of similar vulnerabilities. The manipulation allows gentle data tap from a database (currently supports MySQL/MariaDB only) by means of bit-wise action on printed ASCII fonts by a blind-SQL injection. For inter-operation with additional Python tackles and to allow additional workers to develop the structures delivered in this, the units can be smuggled into other Python-based writings.
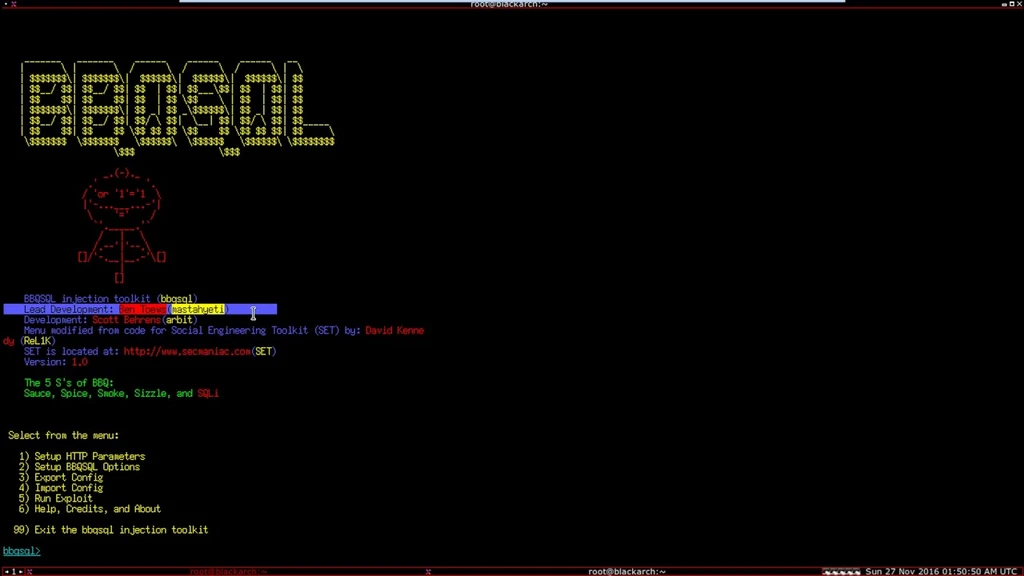
Highlights
- Allows processing for Time-based Blind SQLI on HTTP Shots and the key functions.
- Utilize Blind SQL Injection Vulnerabilities as per need.
- Coexisting HTTP supplication for you.
- You can added/remove anything that is not suited.
3. SQL Inject Me
SQL Inject Me is among the good and secure SQL Injection tools that contain the Mozilla add-on. Through this tool, you can easily scan your searching for websites and applications, and also this tool helps you to get your search from the history if you search it before. Using your search history it provides the results more efficiently. This add-on provides a completely understandable experiment on this exposure.
Highlights
- This is a Firefox addition used to trial for SQL Injection exposures.
- This tool does not try to cooperate with the security of the specified system.
- There is no harbor scanning, box breathing, PIN hacking, or firewall threats via the tool.
4. SQL Sus
SQLSus is another free-to-use and friendly SQL Injection tool and essentially a MySQL injection and coup-up tool. This tool provides an order-based interface which allows you to inject your own SQL Inquiry and do SQL Injection Operations. The language of this tool is Perl, and you can add the features by writing your own codes.
This is the fastest and more efficient tool at this time to use. It is the more strong blind action algorithm injection that can increase the data collection capacity. To get better results, use the stacked sub-queries option. Using multi-threading, you can do the action in multi-threads to make the procedure more efficient.

Highlights
- Compatible with both quoted and numeric injections.
- Databases labels, tables tags, columns titles, table. On MySQL 5, the database construction can be combined in one order from within sqlsus.
- Detect the precise injection space, with all possible limits, as much as it is possible to inject at one time.
- Assist with offer and POST parameters injection courses.
- Funding for HTTP proxy and HTTP modest verification.
5. WhiteWidow
Whitewidow is a free-to-use automatic SQL exposure scanner that is able to execute via file list and can scratch Google for prospective undefendable sites. It permits automatic formatting of files, unsystematic user agents, skill to execute SQL map from the site, IP addresses, information of server, many SQL injection syntax, and a good atmosphere.
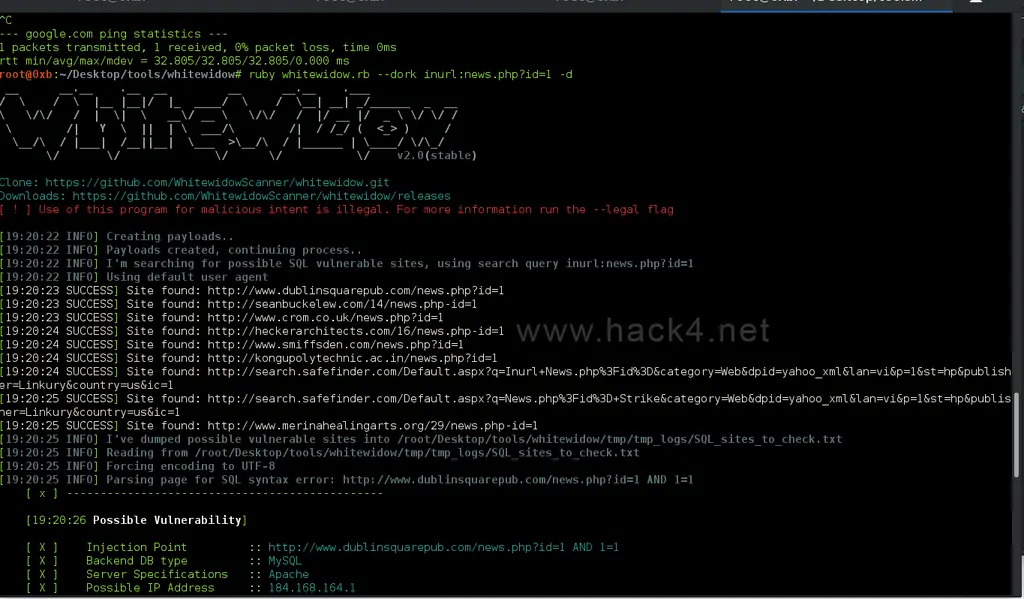
Highlights
- Netsparker Run white Window in pre-setted mode and scratch Google for reliable sites to find random inquiries.
- Execute this via a given file and attach the SQL syntax with the URL.
- It starts the assistance flag with the help menu.
- This can download all required stones and permit you to execute the site without barriers.
6. SQLMap
SQLMap is also good and open to use the SQL Injection tool. It is more famous than all SQL Injection tools that are available in the market to use. This tool is simple to use the SQL injection accessibilities of a web app and adopt the database server. It has a strong analysis engine that can simply analyze many SQL Injections connected with accessibilities.
It assists a massive variety of database servers, including MySQL, Oracle, PostgreSQL, Firebird, Sybase, SAP MaxDB, Microsoft SQL Server, Microsoft Access, IBM DB2, SQLite, and HSQLDB. Many famous database servers are pre-added in this. It also permits numerous types of SQL injection threats, having a boolean-based blind, time-based blind, error-based, UNION query-based, stacked queries, and out-of-band.

Highlights
- Complete assistance for six SQL injection methods.
- Assist straight link to the databank without providing buy a SQL injection.
- Assists to the number of users, databases, tables, password muddles, freedoms, roles, and columns.
- Automated appreciation of password hash arrangements and assisted in rapid using a dictionary-based threat.
7. jSQL Injection
The jSQL Injection is among the best SQLI tools. It is based on Java language and assists IT groups search database information from reserved servers. This tool is free and open to use. It is compatible with Linux, Windows, Mac operating systems, and Java 11-17 version.
This is a good and effective SQLI tool but it has many other scanning susceptibility and saturation. This tool also has Parrot Security OS, ArchStrike, Kali Linux, Pentest Box, and BlackArch Linux. If you are a beginner then this tool my seems a little bit complecated.

Highlights
- Multiple injections like Normal, Error, Blind, and Time.
- Different injection procedures like Default, Zip, Dios.
- Databank fingerprints include basic error, Order By error, single Boolean query.
- Writing sandboxes for SQL and interfering.
- Arrange to inject many missions.
- Read and write files through injection.
8. Burp
Burp is an SQLI web susceptibility scanner with its built-in suites based on the research of PortSwigger to assist users in automatically searching a massive variety of exposures in web apps. Just for the sake of example, the users signify connections, aims, and outer servers to examine unseen threats to conformist scanners, like nonsimultaneous SQLI and blind SSRF.
One of its Suites has the key function that it has the skill to intercept the HTTP desires. When you search on the browser, it directly goes to the server, and when the server processes your request back, it passes the results to you. Your search direct goes to the suite that intercepts the search traffic. A moving algorithm creates a list of its aims in the same way.

Highlights
- Crawl Navigate barriers automatically.
- Find more closed attack grounds.
- Execute Fewer queries; quicker scans.
- Expertness does not disclose security.
- Accessibilities trails for a massive variety of problems.
- Originator Innovation in impulsive scanning.
- Dependability enhance sign-to-racket-ratio
9. Blisqy
Blisqy is another good tool that helps you identify a MySQL/Maria DB after searching a Time-Based Blind SQL injection exposure on a web server. Now, it assists injections on HTTP Headers. You can have to identify an expected Blind SQL injection exposure on a Webserver as detailed on Pentester-Lab (From SQL Injection to Shell II)

Highlights
- It provides the fuzzing or exploitation option to use.
- It also provides the report of injectable trials.
- After searching a time-based SQL, you can prepare the script.
10. Mole
Mole or (The Mole) is among the best and an automated SQL injection tool that is available for free. This is an open-to-use program hosted on Sourceforge. You just have to search the accessible URL and then add it to the tool. This tool can discover the exposure from the given URL by exploiting the union-based or Boolean-based query method.
This tool provides an authority line interface, but the interface is simple to use. It also allows auto-completion on both authorities and authority arguments. So, you can simply use this tool. Mole assists MySQL, MsSQL, and Postgres database servers. Thus, you just have to execute SQL injection threats against these databanks. This tool is designed in Python and needs only Python3 and Python3-lxml.
Highlights
- Assists in SQL Server, Mysql, Postgres, and Oracle.
- Automated SQL injection utilization via union method.
- Automated blind SQL injection utilization.
- Checks SQL Injections in GET/POST/Cookie limits.
- Assists in filters to bypass definite IPS/IDS regulations using general effects and the probability of making new ones quickly.
11. Leviathan
Leviathan is an aggregate audit toolkit that has a massive variety of services to search, brute force, SQL injection discovery, and executing custom exploit abilities. It has free-to-use tools like masscan, ncrack, dsss and provides you relax to using these with an alliance. The main object of this program is an auditing system nationwide or in a huge IP range.
Highlights
- Search FTP, SSH, Telnet, RDP, and MYSQL services executing a limited country or in an IP range via Shodan and Censys.
- You can search services with an incorporated tool named Ncrack.
- You can execute system operations remotely.
- Find SQL injection accessibilities on sites with special national hold or with your customized Google Jerk.
- Find open victims with Shodan, censys, or masscan and huge feat them by giving your own effort or using preadded efforts.
12. Explo
Explo is also among the good and simple tools to detail web safety problems in a manual and automatic format. By identifying a request workflow, it is able to achieve safety problems without the help of creating a script. This offers to share complex searching in an easily readable and run-able format. There you can define file the safety problems is tried by running two steps that are tested from top to bottom. The last process provides success or failure, depending on the string. You have a fault in your SQL syntax to be hunted.

Highlights
- There are a few illustration test cases in the folder.
- You can also have this as a python lib.
- Proxy and a timeout for queries can be set through situations. The default timeout is 15 seconds.
- Modules can include better features and groups of safety problems.
13. Blind SQL BitShifting
Blind SQL BitShifting is a good tool that executes blind SQL injection by bit shifting ways to calculate attributes alternatively of estimating them. It needed 7/8 requests per attribute, based on the verification.
The expect_only_ascii option form the tool that the attributes it is selling are all ASCII. Since the ASCII charset only goes up to 127, we can set the first bit to 0 and not worry about calculating it. That’s a 12.5% reduction in requests. Testing locally yielded an average speed increase of 15%. Of course, this can cause issues when dumping chars that are outside of the ASCII range. By default, it’s set to 0.
Highlights
- This tool can estimate characters instead of analyzing them.
- This provides results in 2-dimensions.
- It processes 7/8 queries on each character.
14. Netsparker
Netsparker is a good web exposure management key that contains SQLi discovery as one of its many functions. It also emphasizes scalability, automation, and incorporation. The suite is created around a web exposure scanner and can incorporate third-party tackles. Workers do not want to be well-informed about the basic code. The company also provides an SQL Injection Rogue Sheet to assist in moderation work.
Highlights
- Automated privacy tasks and protect your team many hours every month.
- Recognize the exposures that actually matter, then flawlessly allocate them for remediation.
- Assists privacy and growth teams grow ahead of their jobs; you execute an AppSec, DevOps, or DevSecOps tool.
- Save exposures by creating more safe code.
Final Words
These are the best SQL tools that we gathered for you to save your search time. These tools are cheap and some are free to use for personal use. However, for the access of premium features, you have to pay for subscription. Some tools are related to your search history and they work more efficiently. You can verify SQL injection exposures on your site through these software tools. You can try all to get the best suited one or more for you according to your requirements. Also, you can share these tools with your friends and family.