Hacking is the act of forcefully entering someone’s system with the intent of violating his privacy or stealing his data. We all know what hacking is, and practically everyone has Wi-Fi at home. And while hacking might not always be for malicious purposes, nowadays it is mostly characterized as unlawful activity by cyber criminals-motivated by financial gain, information gathering (spying), and even just for the “fun” of the challenge.
What does “Wi-Fi” stand for in full? The fact that the term stands for “Wireless fidelity” is a mistake for many of us. It is just a trademark word that refers to IEEE 802.11x, a wireless technology that allows for high-speed wireless Internet and network connections.
List of Wi-Fi Hacking Software
The Internet is the most valued resource available to everyone or any business in today’s society. Access to a fast and robust Internet connection, whether by Wi-Fi, broadband, or another source, is extremely important in our day-to-day lives. With the increased use of Wi-Fi networks, security has become a primary concern for both consumers and service providers, as hackers develop new techniques to breach Wi-Fi connections.
Although Wi-Fi connections are essential to us, they are also costly, and not everyone can afford one. We frequently observe that our neighborhood or business has several Wi-Fi connections, but we need a password to access them. Today, there exist programs that can help us hack Wi-Fi connections and then utilize them to our benefit. The best Wi-Fi hacking tools available for you to use and hack Wi-Fi connections are listed below.
1. WPA WPS Tester
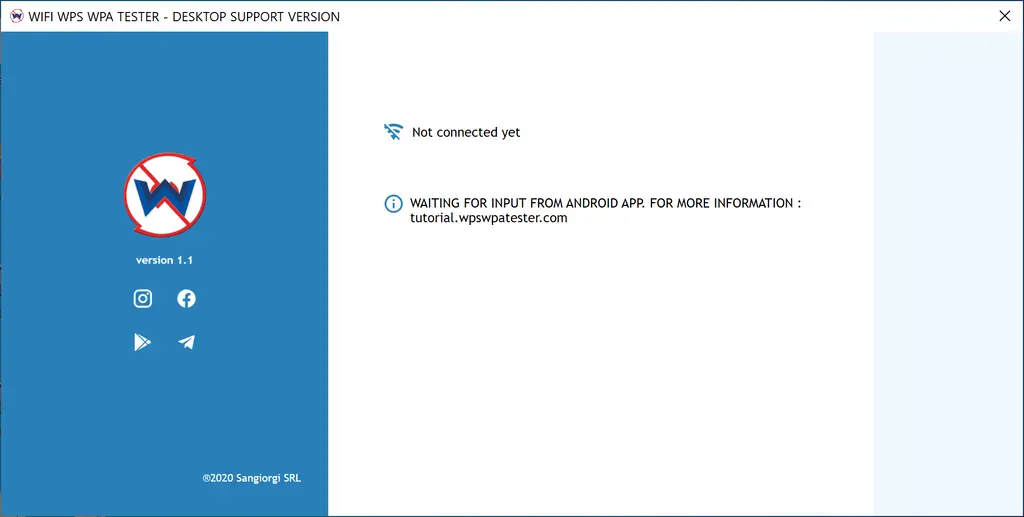
WPA WPS Tester is an application that allows you to examine if your point of access WPS protocol is vulnerable. This check may be performed on any network with this program; however, it is advised that you use it strictly on your own. You will need a rooted smartphone and the ‘Busy Box’ software installed to utilize the app properly. It is a program that has a lot of cool features.
It can help you if you forget your Wi-Fi password. WPA WPS Tester also allows you to view all the passwords for all the Wi-Fi networks you have connected to from your Android device, in addition to helping you evaluate the security of your point of access. It does not work in desktop mode.
2. Kismet
Kismet is a free piece of C++ software that sniffs TCP, UDP, DHCP, and ARP packets. This stand-alone application does not interface with the network. It can locate hidden networks and is utilized for wardriving. The packets recorded may be exported to Wireshark and studied further. It is compatible with Linux, Windows, and a few more operating systems.
Kismet is one of the most well-known Wi-Fi hacking tools. It works with any Wi-Fi card that supports radio frequency monitoring mode and runs on all operating systems (RFMON). It captures packets passively to detect both broadcasting and concealed wireless networks. Kismet works in a different way than other wireless network detectors in that it is passive.
It also has basic wireless IDS capabilities, including identification of active wireless sniffer applications like NetStumbler and many wireless network threats. It can also decode non-802.11 protocols. It is also the most popular and up-to-date open-source wireless monitoring tool available.
3. AirSnort
AirSnort is a popular wireless LAN or Wi-Fi password cracking software. It can break WEP encryption on a wireless 802.11b network. Although the utility is no longer developed, it is still available for download from SourceForge. This program is available in English. The program is available for free and runs on both Windows and Linux. AirSnort was distributed under the GNU General Public License.
AirSnort supports both ORiNOCO (firmware 7.52) and Prism II cards. This utility can be used to crack WEP passwords. It first captures network data packets before retrieving the network’s password through packet analysis. It is a simple but effective device.
It employs a passive assault; it monitors data flow and attempts to obtain information or quantify encryption or password keys upon receiving a sufficient number of data packets without destroying the data. The command-line version uses a simple text screen, while the GUI version lists summary information in its windows.
4. Aircrack-ng
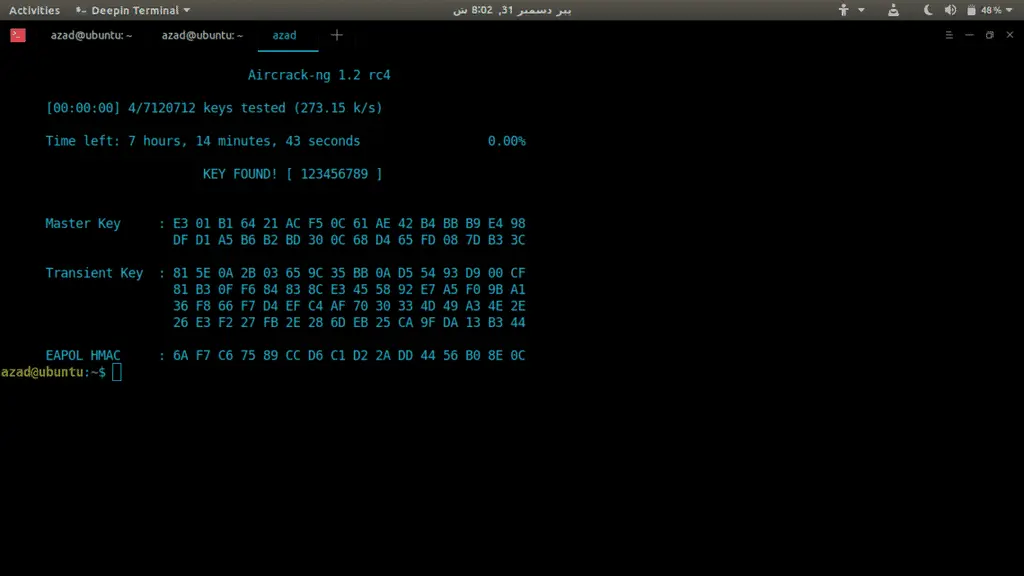
Aircrack-ng is a free wireless password cracking software written in C-language. It can help you crack the passwords by cracking WEP keys of the Wi-Fi 802.11b network. The software focuses on step-by-step monitoring, attacking, testing, and finally breaking the password. By collecting packets, Aircrack uses the best methods to recover wireless passwords. It tries to retrieve the password once it has acquired enough packets.
It uses a normal FMS attack with some tweaks to make it faster. The business that created the application also provides an online tutorial on installing and cracking Wi-Fi passwords. It is available as a Linux distribution, a Live CD, and a VMware image. Any of them will suffice. It is almost certain to operate with the majority of wireless adapters.
Currently, the program is only available in English and uses data packets to crack theWEP and WPA-PSK keys on 802.11b networks. It uses an FMS attack, a PTW attack, and dictionary assaults to crack WEP keys.
5. NetStumbler
NetStumbler is also known as Network Stumbler, and it is a well-known Windows tool to find open wireless access points. It has a trimmed-down version known as MiniStumbler. This tool is free for Windows. After running the program, it will automatically begin scanning the wireless networks in the area.
You will see a complete list of networks in the area when it is completed. It is thus mainly used for wardriving, also known as access point mapping, which is the act of mapping Wi-Fi networks in a locally defined area. This tool can also detect unwanted access points in the selected area of concern.
It can also assist in verifying network setups for Linux, Mac OS X, BSD, Solaris, Microsoft Windows, and other operating systems. It has drawbacks; it can be easily detected by any wireless detection system or device if working in the area. This tool does not work well with the latest 64-bit operating system.
6. Reaver

Reaver is an open-source password cracking tool. It uses a brute force attack against the WPS registrar Pin to recover WPA/WPA2. It attempts every possible combination to guess the AP’s 8-digit PIN. Depending on the target’s AP, Reaver will recover the APs plain text WPA/WPA2 passphrase in 4-10 hours. However, if you are using an offline attack and the AP is vulnerable, it could just take a few seconds or minutes. It is available for Linux.
This tool has been tested against a wide range of access points and WPS implementations and is designed to be reliable and practical. It provides support for the offline Pixie Dust attack. It provides compatibility with all supported Wi-Fi chips; wash now displays the correct signal level with all the (supported) Wi-Fi chips. Reaver for Android also supports external scripts.
7. WifiPhisher
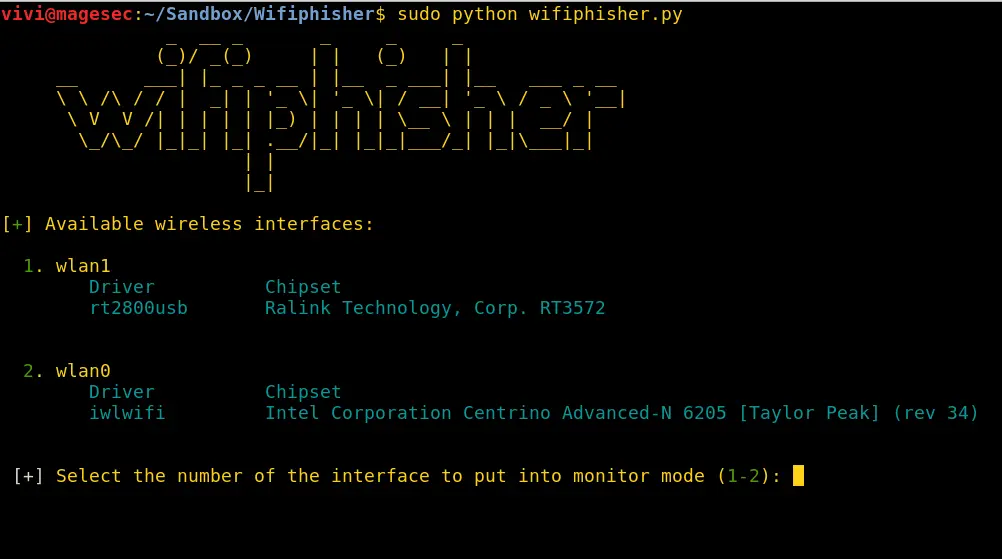
WifiPhisher is a security tool that launches automated phishing attacks on wireless networks to get secret passphrases or other credentials or infect the victims with malware. It does not use attacks like brute force; instead, it relies on social engineering techniques. It can run for hours inside a Raspberry Pi device, executing all modern Wi-Fi association techniques (Evil Twin, KARMA, and Known Beacons).
It has a set of community-driven phishing templates available for different deployment scenarios. Users can also write Python-driven scripts to create new phishing scenario templates. There are a lot of phishing templates of drivers and router firmware updates that are ready to use. It offers an interactive textual interface that is a relief from the ordinary command-line provided by other tools.
WifiPhisher’s developers introduced state-of-the-art assault methods, including Known Beacons and Lure10, and other incredible tactics, which were quickly implemented into the tool.
8. Fern WIFI Cracker
Fern WIFI Cracker is a wireless attack software designed to break WEP/WPA/WPA2/WPA2 keys on Wi-Fi networks. It employs several methods, including exploiting insecure protocols, phishing attacks, brute-force, and dictionary-based password guessing assaults. Fern is compatible with Windows, Linux, and Mac OS X.
Fern operated on a freemium model, meaning that a license was required to access the complete set of services. It launches WPA/WPA2 Cracking attacks with Dictionary or WPS. It automatically saves the keys on successful crack. It is written using Python programming language and the Python Qt GUI library, and this ethical hacking program can run different network-based attacks on Ethernet and wireless.
It supports WEP Cracking with Fragmentation or WPS attack. It is designed to test and discover flaws in one’s network, aiming to fix the flaws. It has an automatic Access Point Attack System and Passive and Ethernet Modes.
9. WireSHARK
WireSHARK is supposed to be user-friendly, but it has a lot of power below the hood. It will be useful if you are familiar with network protocols and can successfully analyze the traffic you are seeing. It is the most commonly used network analyzer on the market. It is a GUI-based utility available for Linux, Mac, and Windows. It checks the traffic going across your network using packets collected by WinPcap and Libpcap.
The utility gathers and displays the micro-level informatio n of the packets. Because the number of packets collected might be large, the program allows you to filter them based on protocol type, strings, and other criteria. This tool might be quite useful if you know what you are looking for.
WireSHARK is a protocol analyzer for networks. It allows the users to monitor what is going on in their network. You may collect packets in real-time, study them at a high level, and look at the values of specific fields inside a packet.
10. Kali Linux NetHunter

Kali Linux NetHunter is an open-source andfree tool that allows you to perform mobile penetration testing on Android smartphones. This platform is built on the Kali Linux operating system. It is compatible with a number of Android devices. This platform supports practically all Android devices on the market, including some high-end devices like the OnePlus One, Samsung Galaxy S, and Google Nexus.
This platform is typically maintained by a volunteer community, with project funding provided by Offensive Security. NetHunter also includes a complete Kali Linux toolset with many tools available via a simple menu. Wireless 802.11 frame injection and one-click MANA Evil Access Point deployment are among the technologies available for Wi-Fi hacking and mobile penetration testing.
The configuration interface in Nethunter allows you to manage the complicated configuration files. Kali NetHunter is a must-have Android hacking tool, thanks to its kernel.
11. Cain & Abel
Cain & Abel is another popular app on the list of tools to retrieve Wi-Fi passwords, which is a good way of saying hacking. It is called after Adam and Eve’s offspring. It employs a variety of approaches, including researching and analyzing each data packet separately, decoding scrambled passwords, and brute-force, dictionary, and cryptanalysis assaults.
This app is compatible with multiple versions of Microsoft OS. The program can also inspect wireless data and obtain wireless network keys by recognizing cached passwords and evaluating routing security information. A recently introduced hacking function is Address Resolution Protocol (ARP) support for detecting switched LANs and MITM attacks.
You may also record Voice over Internet Protocol (VoIP) chats with the Windows Wi-Fi hacking program if this is not enough. This is the tool that security consultants, professional penetration testers, and anybody else who wants to use ethically and not cheat on anyone for illegal password access recommend and utilize.
12. WepAttack
WepAttack is an open-source Linux WEP key hacking tool for breaking 802.11 WEP keys. This tool uses an active dictionary attack to discover the working key by testing millions of words. The attack is active in nature and not passive. The device will test the dictionary words to get the working key. It needs a dumpfile for attacking networks.
If Kismet captures network data, a dumpfile is generated automatically. This file can be supplied to WepAttack in the format “Kismet-[date]-[no].dump.” To use WepAttack, all that is required is a functional WLAN card, which is found on almost all computers. It is also used to monitor the data traffic from a network. It is compatible with the Windows system and requires minimum hardware.
13. Zanti

Zanti was developed by Imperium Mobile Security for cyber security professionals. It is a well-known hacking app that allows network security professionals to assess risk levels. This simple mobile penetration toolkit can examine and penetrate Wi-Fi networks. Its Wi-Fi scanner displays access points in green that have a recognized default key setup. The program can also kill connections, preventing the target from accessing any website or service.
You can find the gaps in your network and make repairs by mimicking the procedures employed by cyber attackers. MITM attacks, vulnerability scans, password auditing, scanning, Mac address spoofing, and more are all possible with this software. It performs multiple tasks. It is an excellent hacking toolkit for Android users.
It carries out a wide range of network scans of different intensities to identify connected devices, properties, and vulnerabilities. It extracts reports and shares them with zConsole, and this service allows the developers to identify the security breaches. Its drawback is that it runs only on a rooted device.
14. Wifite
Wifite is a tool to audit WPA or WEP encrypted wireless networks. Wifite was created to work with Linux distributions like Kali Linux, Pentoo, and BackBox and any Linux distribution with wireless drivers patched for injection. Ubuntu 11/10, Debian 6, and Fedora 16 work with the script.
Wifite must be run as root to work; this is required by the software package it employs. It is not a good idea to run downloaded scripts as root. Wifite implies you have a wireless card and the necessary drivers installed on your computer. Virtual Machines cannot contact hardware directly; hence a wireless USB dongle is required.
It sorts targets by signal strength (in dB); cracks closest access points first. It automatically de-authenticates clients of concealed networks to reveal SSIDs. Several filters specify exactly what to attack (WEP/WPA/both, above particular signal strengths, channels, etc.). It also displays the session summary at the exit.
15. WPS Connect

WPS Connect is the most powerful program that allows you to connect to any WPS-enabled router. This application is accessible for free and is simple to use and download. Its goal is to see if the router in question is vulnerable to a PIN by default. Many internet service provider-installed routers are vulnerable. You can use this program to see if your router is vulnerable and change the password if necessary.
To hack the Wi-Fi pin, it employs password methods such as Zhao or easyboxPIN. This Wi-Fi hacking tool can inspect any router and determine whether it is vulnerable to malicious assaults. WPS Connect uses powerful algorithms to crack the Wi-Fi password. It helps to examine or scan any router. Your smartphone must be rooted to use WPS Connect. WPS Connect is an excellent tool for determining whether or not your router’s password is completely secure, though it has many other applications.
Final Word
In most areas, attempting to obtain unauthorized access to wireless networks is unlawful. If you wish to practice with these tools, do so on a wireless network that you own or have access to through the network owner’s authorization. Network administrators and programmers who deal with Wi-Fi-based applications use wireless monitoring and troubleshooting tools.
When some of your systems have trouble connecting to the network, these tools can help. Red teamers and penetration testers looking for possible weaknesses to attack can benefit from them. Knowing how to use a few different wireless hacking tools may be an excellent investment in your ethical hacking career.